Medical device manufacturers continue to develop new, highly sophisticated and increasingly connected products. These products offer a wide range of benefits: Improved treatments, more precise diagnostics, better patient monitoring, automated control, and central reporting and monitoring of data.
This increased connectivity, however, comes with risks for both patients and providers.
Even though these companies are heavily investing in the development of new medical device technologies, they often lack the security expertise and resources to ensure high levels of security are built into these products. Many devices employ new protocols, platforms and middleware solutions that have not been thoroughly vetted for security issues. The result, not surprisingly, is a slew of devices that are easily compromised by hackers.
We continue to see headlines of new security vulnerabilities found in critical medical devices. Ransomware attacks have targeted hospitals and medical providers with alarming success. In these kinds of attacks, hackers compromise a system, encrypting critical data so the systems cannot operate, then require a ransom payment to restore the system to working order.

Past ransomware attacks have targeted IT and database systems, but future attacks may focus on medical devices. In fact, in 2019, cybersecurity experts found dangerous vulnerabilities in the technical design of some insulin pumps, prompting the FDA to issue a warning that hackers could compromise insulin pumps by connecting to them via WiFi and changing the pump’s settings to either under- or over-deliver insulin. If hackers are able to control systems that impact patient outcomes, they will have tremendous leverage for their ransom demands.
Use of multiple layers of protection, including firewalls, authentication, security protocols and intrusion detection/intrusion prevention, is a long-established driving principle for enterprise security. In contrast, most medical devices lack basic firewalls or security protocols, and often rely on little more than simple password authentication. There was an assumption that these devices are not attractive targets to hackers, or are not vulnerable to attacks, but that is no longer valid. Attacks against all types of embedded devices, including medical products, are on the rise, and greater security measures are now needed.
For more than 25 years, cybersecurity has been a critical focus for large enterprises. Now medical device design engineers need to take a page from the enterprise security playbook.
Embedded Security Challenges
Medical devices are very different from standard PCs. They are fixed-function devices designed to perform a specialized task. Installing new software on the system in the field often requires a specialized upgrade process or is simply not supported. These devices are optimized to minimize processing cycles and memory usage, so they lack extra processing resources. PC security solutions won’t solve the security challenges of these devices.
Challenges for medical device security include:
- Critical functionality: Medical devices control life-enabling systems and manage sensitive data.
- Replication: Once designed and built, medical devices are mass produced, resulting in thousands to millions of identical devices. Once discovered, a successful attack against one of these devices can be replicated across all the devices.
- Security assumptions: Many medical device engineers have long assumed that their products are not targets for hackers and have not considered security a critical priority.
- Patching limitations: Most medical devices are not easily upgraded. Once they are deployed, they will only run the software that was originally installed at the factory.
- Long lifecycle: The lifecycle for medical devices may be as long as 10, 15 or even 20 years. Building a device that will stand up to the security requirements of the next two decades is a tremendous challenge.
- Deployed outside of the enterprise security perimeter: Medical devices may be mobile or may be deployed in the home, environments lacking the protections found in a corporate environment.
- Siloed: No way for the end user to easily monitor the device’s security health or make changes.
Cyberattacks and The Motivated Hacker
The level of security required for a medical device varies depending upon the function of the device. Rather than asking if the device is secure, OEMs should be asking if the device is secure enough. A robotic surgical system clearly needs a very different level of security than sensors equipped with communication capability for remote monitoring of patients.
Hacking is not just the domain of bored teenagers, hacking drones, or even the small groups of motivated hackers. When the stakes are high enough, cyberattacks are typically multi-phased, multi-year efforts that are carried out by large, well-funded teams of hackers.
We are no longer talking about protecting a device from just malformed IP packets or DoS packet floods. Hackers often have detailed information about the device they are targeting and have sophisticated toolkits and skills that can be used to develop attacks.
Have you considered how to protect devices from attack by a group with detailed knowledge of the inner workings of your product?
FDA Cybersecurity Guidelines
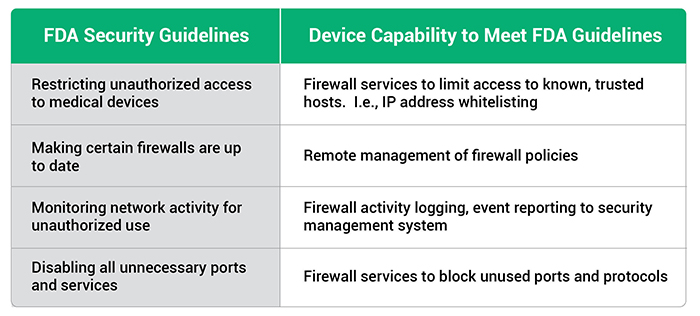
The FDA has issued guidance for OEMs building medical devices. A few of the capabilities recommended in the FDA guidelines include:
- Restricting unauthorized access to medical devices
- Making certain that firewalls are up-to-date
- Monitoring network activity for unauthorized use
- Disabling all unnecessary ports and services
As an engineer working on a medical device, what do these guidelines mean? Many medical devices are specialized products and the security solutions used for standard PCs often won’t work for specialized devices. Clearly, meeting the security guidelines is important. Doing so requires an approach that is customized to the needs of the device.
Security Requirements for Medical Devices
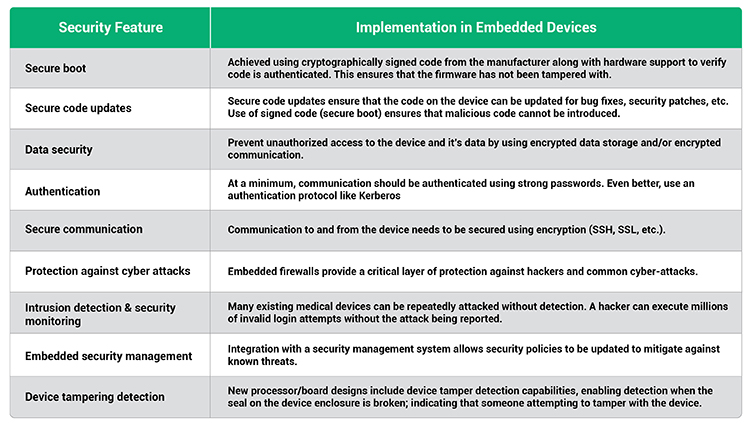
A security solution for medical devices must protect firmware from tampering, secure the data stored by the device, secure communication, and protect the device from cyberattacks. This can only be achieved by building in security from the early stages of design.
There is no “one-size-fits-all security solution” for medical devices. Engineers must take into consideration the cost of a security failure (economic, environmental, social, etc.), the risk of attack, available attack vectors, and the cost of implementing a security solution. Table I outlines the features that need to be considered.
Integrating Security into The Device
Building protection into the device itself provides a critical security layer that ensures devices are no longer depending on the corporate firewall as their sole layer of security and allows security to be customized to the needs of the device. The engineering team must be as focused on security as they are on the new capabilities of the device. Building security capabilities into a medical device will enable the device to meet the FDA security guidelines.
Summary
Today’s modern medical devices are complex, connected computing devices that perform critical functions. Including the latest security protocols and technologies in these devices is an essential design task. Medical device manufacturers must consider security features at the very beginning of the design process to ensure the device is protected from the likelihood of advanced cyber threats.






