In the life sciences industry, one of the greatest advancements of the 21st century has been the expanded use of technology for research and patient care, specifically the adoption of connected devices for diagnostic testing, storing and sharing data, and patient monitoring. These innovations decrease costs for providers and patients and expand the accessibility of care for everyone, including low-income patients and those in geographic regions with more limited access to care. Other technologies, such as remote patient tracking and monitoring, are also fueling this technological movement. Patient devices can now communicate with each other, store information on the cloud, and collect vitals without the intervention of doctors or nurses. This groundbreaking technology is called the Internet of Medical Things (IoMT).[i]
IoMT is the connection of medical devices via computer networks that allows for ongoing communication and data sharing. IoMT stems from the development of Internet of Things (IoT) technology that includes networks of physical objects that communicate through embedded sensors and software. An example of IoT technology is a smart home in which lights, doors, cameras, locks and other functions are controlled with a smartphone, which also collects data.[ii]
Examples of IoMT devices include smart pills with ingestible sensors, emergency response systems, wearable devices for remote patient monitoring, wheelchair sensors and CT scanners connected to smart apps, among many others. Even though many IoMT devices are in use, this technology is just beginning to take off, and it likely will continue to revolutionize the patient care process.[iii]
Privacy and Security Concerns
Although IoMT technology can provide numerous benefits for both patients and providers, it comes with added risk for life sciences organizations. Specifically, by using these devices, organizations increase the amount of protected health information (PHI) collected, transferred, maintained and stored—all of which increases inherent risk, especially when considering the pervasive use of third parties within these ecosystems.
Companies need to prepare for a high volume of cyberattack attempts as they increasingly rely on this technology for everyday patient care. In addition, patients’ lives depend on some of these devices for essentials such as oxygen and medicine delivery. These risks and safety concerns will require that technological upgrades emphasize both protection against hackers who seek to manipulate the devices and the protection of patient data to prevent noncompliance with the Health Insurance Portability and Accountability Act of 1996 (HIPAA) and other relevant privacy regulations.
Per HIPAA, the European Union’s (EU’s) General Data Protection Regulation (GDPR) and other privacy standards, IoMT device manufacturers must follow specific security guidelines outlined in the IoT Cybersecurity Improvement Act of 2020. This act set government standards for IoT devices and tasked the National Institute of Standards and Technologies (NIST) with developing a set of standards for the use, management and security protection of all IoT devices used by any federal government agency or organization that accesses government databases.
This act prohibits any government agency from purchasing or using a device that does not follow the NIST IoT framework. Because the federal government is one of the world’s largest healthcare consumers, this act has a significant downstream impact for IoMT industries. To avoid losing the federal government as a customer, manufacturers must meet the NIST cybersecurity standards.[iv]
In addition to NIST, the FDA also plays a role in regulating the security of medical devices under the Federal Food, Drug, and Cosmetic Act (FD&C Act). Most recently, the FD&C Act was amended to address growing concerns of hacking and ransomware attacks on medical devices connected to the internet. These new guidelines became effective on March 29, 2023.
Before bringing a new device to market, medical device manufacturers are required to:
- Establish a plan to “monitor, identify, and address…postmarket cybersecurity vulnerabilities and exploits.”
- “Design, develop, and maintain processes and procedures to provide a reasonable assurance that the device and related systems are cybersecure”; manufacturers also must issue updates after devices launch to provide and maintain visibility regarding vulnerabilities and uncontrolled risks.
- Provide a “software bill of materials, including commercial, open-source, and off-the-shelf software components.” [v]
The EU and the United Kingdom have also passed regulations related to IoT device security that set similar security standards.[vi]
Although new guidelines are security focused, they help to protect the privacy of the patient personal information stored on IoMT devices. In fact, numerous overlaps exist between privacy and security, as reflected in the following graphic.
Synergy Between Privacy and Security
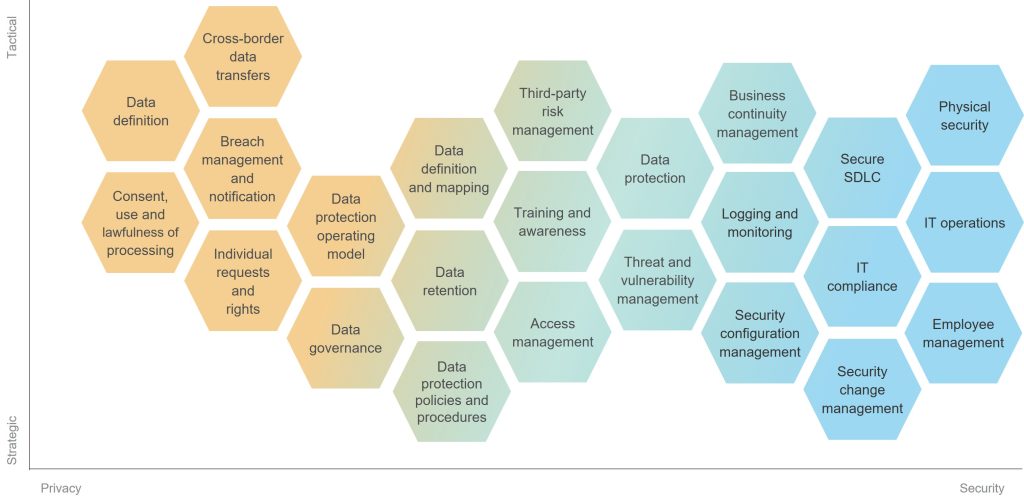
Privacy and Security Best Practices
Following are five best practices for securing IoMT devices to prevent data exposure and respect patient privacy.
- Data minimization. Data minimization refers to limiting the collection of personal data to what is strictly necessary. In addition, organizations should only retain the data long enough to fulfill the stated purpose. Shifting the culture and mindset of an organization toward data minimization could minimize the risk exposure and create a more intentional data collection process.[vii]
- Pseudonymization of data. Pseudonymization of data is a data management technique that separates data identifiers and replaces them with artificial identifiers (pseudonyms) to de-identify the data. With this approach, data cannot be used to identify an individual unless it is paired with additional information.[viii]
Pseudonymization prevents adversaries and other third parties from being able to identify patient data, which mitigates risk by making it harder for a hacker to tie patient data to a specific individual. In addition, pseudonymization is specifically called out in GDPR articles 25(1) and 32(1) as an appropriate technical and organizational measure for upholding privacy by design and data minimization techniques.[ix] - Vendor management and review process. With the growth of IoMT technology, many organizations must outsource areas of their manufacturing, development and storage processes to increase efficiency and offer top-tier products. Outsourcing is beneficial, but it adds additional privacy and security risk by bringing in a third party that might have access to PHI.
Organizations must consider data protection measures and cybersecurity practices during the vendor selection and evaluation process. In addition, vendor management involves regularly checking in with and reassessing vendors to establish that they are maintaining the data privacy expectations set by the life sciences organization. Specifically, it is crucial that vendors use data encryption to minimize threats of breaches and data leakage. Failure to properly manage and assess vendors based on these standards increases an organization’s risk for regulatory scrutiny, breaches, consumer distrust and negative publicity.[x] - Backup procedures. One of the greatest security concerns of medical devices is related to availability. Many IoMT devices are critical to patient care. If a cyberattack were to cause devices to go offline, then patients’ lives could be at risk. Therefore, it is important for providers to have reliable fallback procedures should hackers compromise the functionality of active medical devices. In addition, these alternate procedures should be regularly tested, and employees should be trained to verify preparedness in the event of a cyberattack.
- Transparency. The final—and arguably most important—data privacy best practice when implementing new IoMT technology is to be transparent with patients. IoMT technology is new and exciting both for providers and patients. However, it is important to be clear with patients about the added risks associated with these technologies and the ways in which the company is hedging against these risks. Patients are at the core of life sciences companies. With transparency comes trust, and with trust comes retention. Companies can demonstrate transparency with patients by providing the details of who their data will be shared with, the benefits and risks of new technology, and what specific tactics are in place to keep their information safe.
IoMT technology will only continue to grow and improve patient care, but without strong consideration of privacy and security best practices, this technology could harm patients just as much as it helps them. While it is tempting and exciting to be an early adopter for IoMT technologies, it is the responsibility of life sciences organizations to put patients’ health and safety first. Therefore, it is important to be strategic in the adoption of new technology, adhere to strict privacy and security principles, and be cognizant of the market’s response.
References:
[i] “Top 10 Benefits of IOMT in the Sector of Healthcare,” Folio3 Digital Health, June 9, 2021, https://digitalhealth.folio3.com/blog/benefits-of-iomt/
[ii] Patrick Schneider and Fatos Xhafa, “IoT Data Streams: Concepts and Models,” ScienceDirect, 2022, www.sciencedirect.com/topics/computer-science/internet-of-medical-things
[iii] Ben Lutkevich and Alex DelVecchio, “Definition: Internet of Medical Things (IoMT) or Healthcare IoT,” TechTarget, March 2023, www.techtarget.com/iotagenda/definition/IoMT-Internet-of-Medical-Things
[iv] IoT Cybersecurity Improvement Act of 2020, H.R. 1668, 116th Congress, Dec. 4, 2020, www.congress.gov/bill/116th-congress/house-bill/1668
[v] Center for Devices and Radiological Health and Center for Biologics Evaluation and Research, “Cybersecurity in Medical Devices: Refuse to Accept Policy for Cyber Devices and Related Systems Under Section 524B of the FD&C Act: Guidance for Industry and Food and Drug Administration Staff,” U.S. Food and Drug Administration, March 2023, https://www.fda.gov/regulatory-information/search-fda-guidance-documents/cybersecurity-medical-devices-refuse-accept-policy-cyber-devices-and-related-systems-under-section
[vi] “IoT Cybersecurity: Regulating the Internet of Things,” Thales Group, June 2021, www.thalesgroup.com/en/markets/digital-identity-and-security/iot/inspired/iot-regulations
[vii] European Data Protection Supervisor, “European Data Protection Supervisor Glossary,” https://edps.europa.eu/data-protection/data-protection/glossary_en
[viii] Data Protection Commission, “Anonymisation and Pseudonymisation,” https://www.dataprotection.ie/en/dpc-guidance/anonymisation-pseudonymisation
[ix] Luca Wintergerst, Mike Paquette, and Dale McDiarmid, “Protecting GDPR Personal Data with Pseudonymization,” Elastic, March 27, 2018, www.elastic.co/blog/gdpr-personal-data-pseudonymization-part-1
[x] Madeline Clarke, “Why Is Third-Party Risk Management Important?” CIO Insight, Feb. 15, 2023, www.cioinsight.com/security/third-party-risk-management/







